GoPhish is a freely available framework for conducting phishing campaigns, typically used to test the awareness of company employees to prevent real attacks using phishing as an entry point to gain access or infect endpoints with malware.
It is used by cybersecurity specialists to conduct pentests, but it is also used by hackers.
Tracked phishing assets by malwareleaks app.
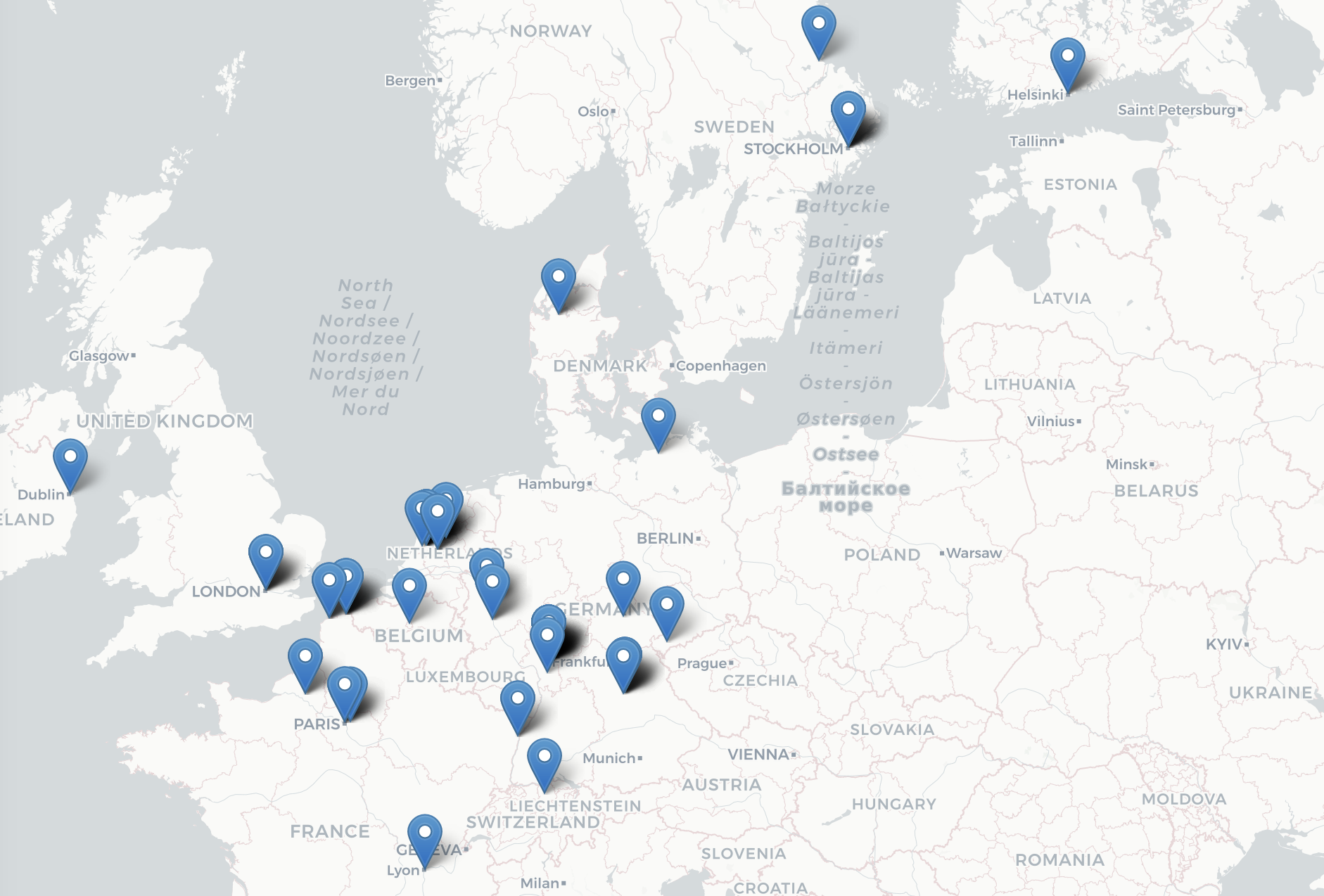
This tool is not malicious, in the hands of bad guys it allows for mass capture of credentials through phishing campaigns.
Phishing itself is a fairly dangerous attack vector.
If we take ordinary users, when they enter logins and passwords on a fake website, this can have many negative consequences, ranging from losing access to the account to being part of a large hacker attack.
For companies, the leakage of account data poses an even greater threat; this can manifest itself as a leak of important information, corporate data, unauthorized access to systems, and loss of financial data.
There are many techniques you can use to protect yourself from phishing:
- use multi-factor authentication (2FA)
- check emails and links you receive carefully
- use protection
Also, if we talk about more comprehensive protection for blocking phishing resources, it is worth paying attention to tools that improve security, including the following:
- SIEM
- IDS/IPS
- Firewall
- Solutions that allow you to analyze logs
For example, a simple solution for blocking phishing IPs using iptables
for ip in $(cat phishing_ips.txt); do
iptables -A OUTPUT -d $ip -j DROP
done
Monitoring using the following Suricata rule
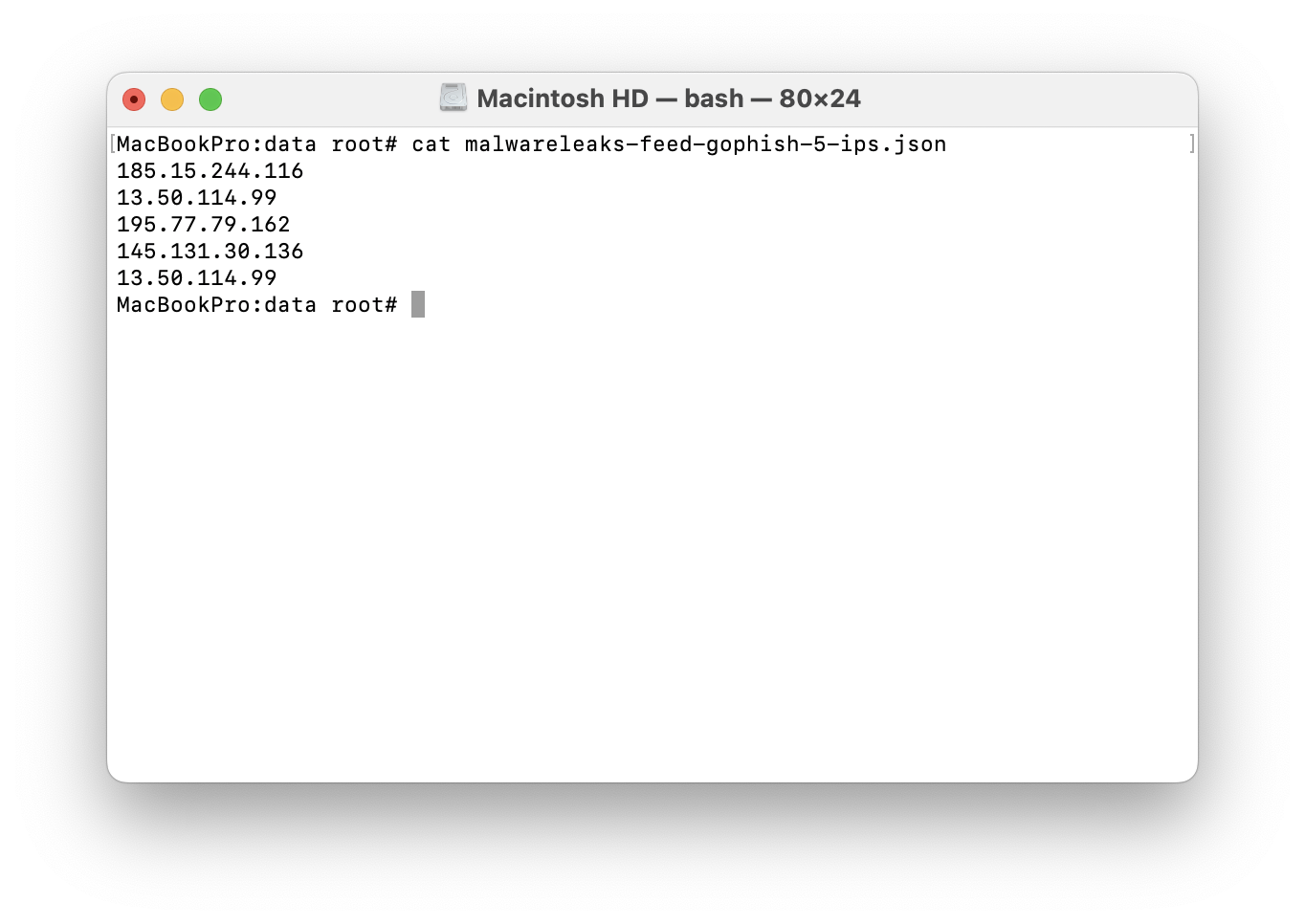
alert ip any any -> [185.15.244.116,13.50.114.99,195.77.79.162] any (msg:"Phishing IP detected"; sid:100001;)Using security tools and approaches to detect malicious activity, you can proactively detect threats, respond to them, and reduce response time to existing cyber incidents.