Defend the digital landscape against evolving cyber threats
Deep dive into hackers infrastructure
malwareleaks is a cyber intelligence platform that actively detects and analyzes malicious infrastructure, including C2 servers, phishing systems, and malware nodes. It provides independent, technical intelligence for proactive threat hunting and early-stage detection.
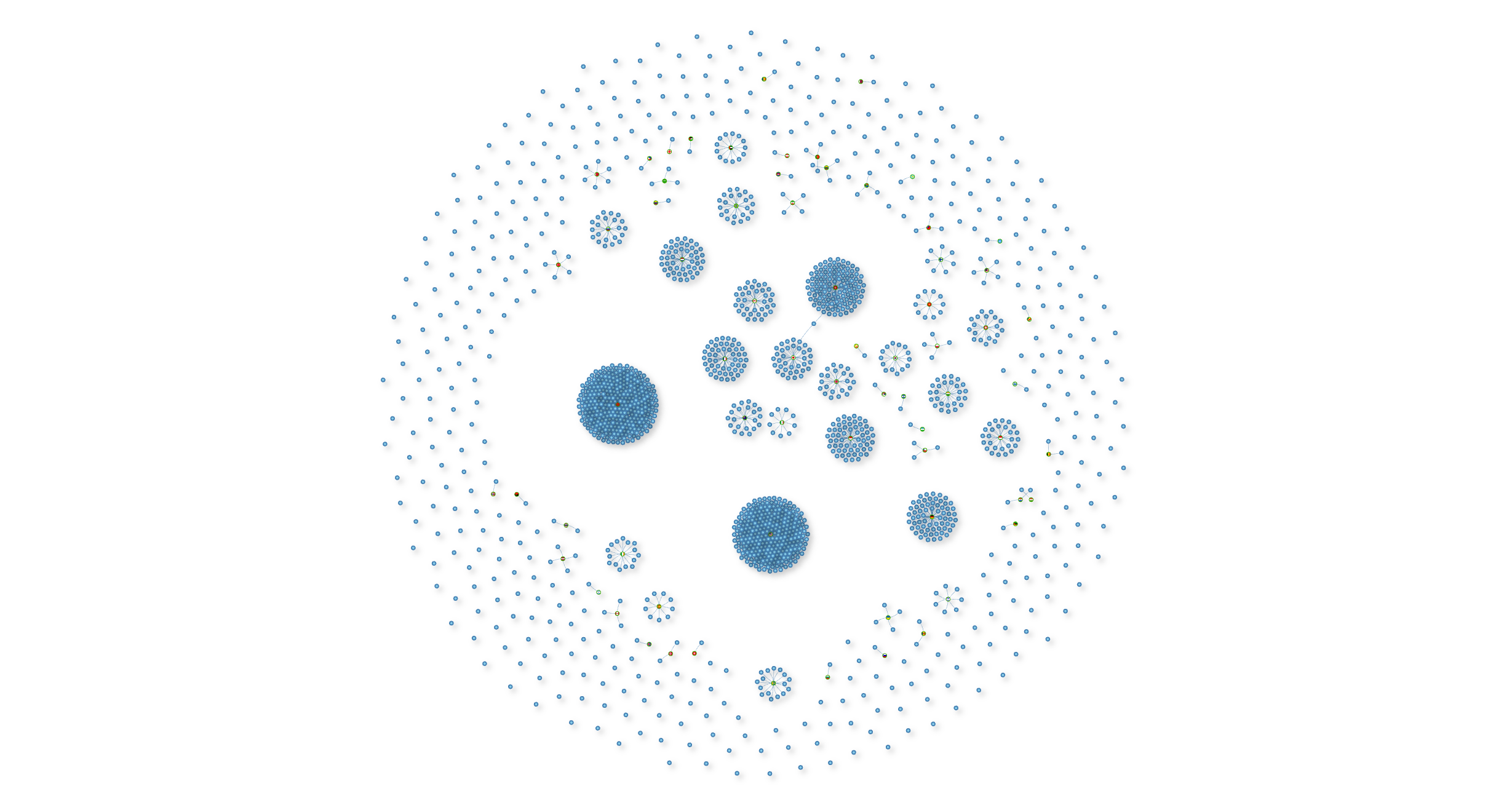
The Threat Map visualizes malicious infrastructure activity in real time, supported by an interactive infrastructure graph and dynamic dashboards for seamless analysis.
Threat Actor graph modeling.
Threat Actors
malwareleaks provides early visibility into new threat actors and tools, enabling security teams to anticipate attacks and strengthen defenses before these threats are widely exploited.
API integration
The platform provides direct API integration, enabling automated, real-time access to up-to-date threat intelligence data, including indicators of compromise (IoCs) and related artifacts, for further analysis, correlation, and integration with existing security systems.
Threat Context & Attribution
Detailed threat actor profiling with MITRE ATT&CK mapping and STIX-compliant objects. A formal relationship graph links actors, tactics, and infrastructure, while attribution logic helps analysts trace adversary operations and uncover attack patterns.
Threat Hunting & Investigation
Deep pivoting from IP addresses to domains, threat actors, and geolocation enables seamless exploration of related infrastructure. One-click investigative navigation, combined with an interactive infrastructure graph, streamlines threat analysis, while advanced filtering and complex query capabilities support precise investigation across large-scale datasets.
Integration and automation
STIX 2.1 export ensures standardized and reliable threat intelligence objects. Seamless synchronization with OpenCTI and MISP enables efficient intelligence sharing across enterprise CTI environments. Automated Telegram integration delivers real-time threat updates, interactive maps, and alerts directly to analysts’ communication channels.
Trend & Predictive Analytics
Interactive dashboards deliver trend and predictive analytics, providing analysts with real-time insights into evolving threats and potential attacks.
Dark Web Monitoring
Scanning dark web sources to detect leaked or stolen sensitive information
Threat Feed
Integrating threat IoCs into security systems allows real-time threat detection and automated blocking of suspicious activity.
Explore the threat.
Stay ahead of cyber attacks by identifying malicious IoCs, IP, domains and malware leaks before they cause harm.
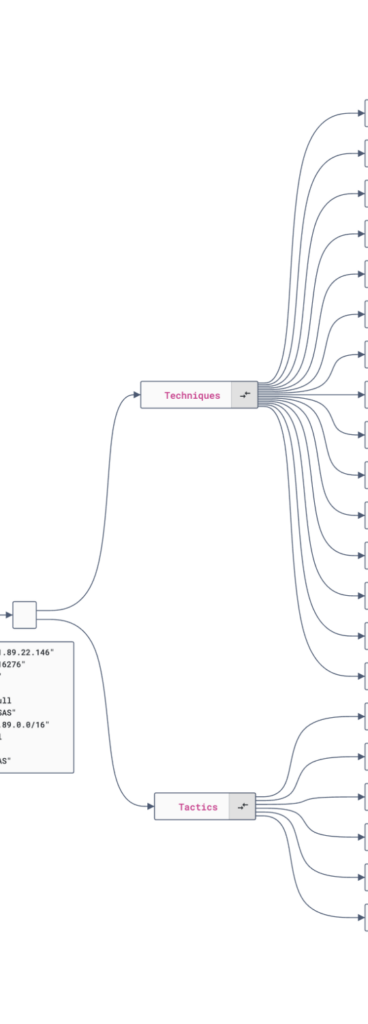
Proactive Threat Intelligence
Try malwareleaks
Test all core features and see how the platform helps you solve real problems